Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, re-mediating, and mitigating" software vulnerabilities. Vulnerability management is integral to computer security and network security, and must not be confused with Vulnerability assessment.
Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities, such as open ports, insecure software configurations, and susceptibility to malware infections.
Correcting vulnerabilities may variously involve the installation of a patch, a change in network security policy, reconfiguration of software, or educating users about social engineering.
https://en.wikipedia.org/wiki/Vulnerability_management
When you start to evaluate your vulnerability management program it's important to look at key categories to have an effect vulnerability management program.
Cost Benefit Analysis:
What is the best bang for your buck? Knowing your budget and scope of what needs to be accomplished will determine what solutions will be included in your analysis. There are a lot of great vulnerability management tools and you will have to determine the key feature sets across multiple tools. Once you have a list of solutions that will work, cost will determine the winner.
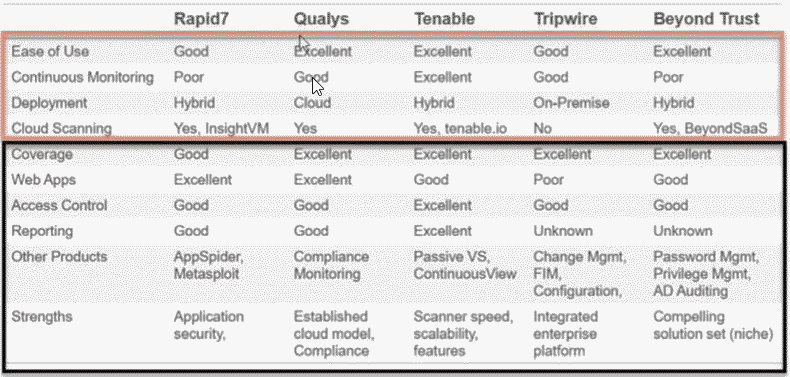
Proof of Concept (How well does each solution work):
When you have your top two or three solutions from your cost benefit analysis you have to put them to the test. A security engineering team will install each solution and test how effective each solution is in the network environment. Having well priced solution doesn't always mean it's the best solution. It's important to test each tool before purchasing. It's also very important to reach out to peers and see if they use or have tested each solution. One metric that gets overlooked is customer service after purchase and peers do a great job of letting you know how well a vendor supports their solution.
Ease of Management:
Being able easily deploy and manage hardware and software is a key driver in an effective vulnerability management program over time. Hardware hasn't become completely obsolete, but cloud solutions are becoming more cost effective. Vulnerability solutions often require both on premises and external scanning capabilities. Being able to see your environment externally and internally on your network lets you know how much time your have to re-mediate a vulnerable host.
A security operation team won't have access to most devices on the network. A vulnerability management solution should allow for asset owners to management their computing environment. This will allow much faster remediation of a know vulnerability. In a day where threats happen quickly, it's a must to have fast remediation with shared responsibly across your organization.
Reporting:
Reporting to governance a complete picture of how cost effective the vulnerability management program has become over time, is a must. Governance will know from the cost benefit analysis in the beginning if the program is on track and when it need to be re-evaluated. This will complete the life-cycle of a vulnerability management program.
Summary:
Requiring a new solution to be put in place across your entire organization isn't an easy task and shouldn't depend on the cheapest solution. Planning and testing in the beging of a life-cycle will save your organization time and money.